Approaches to Message Authentication
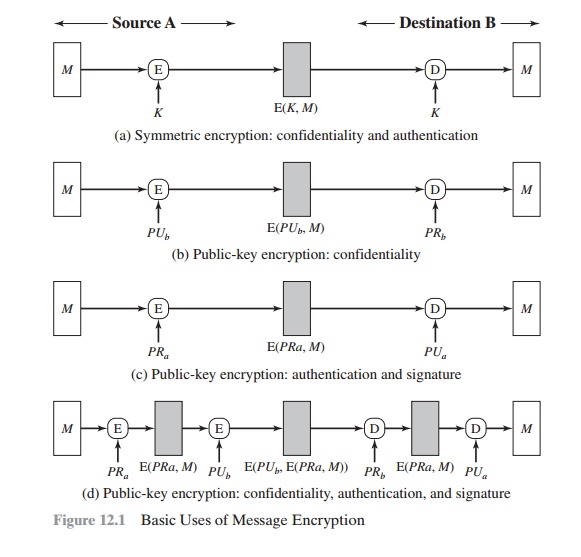
The first approach uses public-key encryption which means the user must provide a public key a message that gives the user permission to. For establishing MAC process the sender and receiver.

Public Key Cryptography And Message Authentication Ppt Download
Three approaches to message authentication.

. This is the short piece of inf What properties. Message authentication code Message encryption Hash function. 31 List three approaches to message authentication.
Message authentication is to protect the message integrity and to perform sender authentication. 31 List three approaches to message authentication. Message Authentication without Message Encryption We examine several approaches to message authentication that do not rely on encryption.
Includes a timestamp the receiver is assured that the message has not been delayed beyond that normally expected for network transit. 34 What properties must a hash function have to be useful for message. A digital signature is a process used for message authentication.
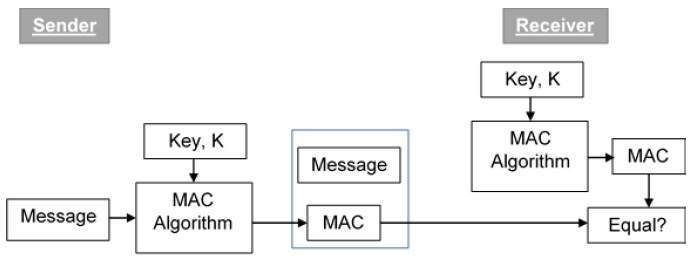
32 What is a message authentication code. 3A messages origin and nature are verified using the message authentication code MAC often. 32 What is a message authentication code.
31 List three approaches to message authentication. 31 List three approaches to message authentication. 32 What is a message authentication code.
32 What is a message authentication code. 31 List three approaches to message authentication. 31 List three approaches to message authentication.
31 List three approaches to message authentication32 What is a message authentication code34 What properties must a hash function have to be useful for message. 34 What properties must a hash function have to be useful for message. Message authentication allows VTAM to determine if a message has been altered in transmission between the session partners.
A code is attached to each message by the sender. The desired three approaches. 34 What properties must a hash.
Message Authentication Code MAC MAC algorithm is a symmetric key cryptographic technique to provide message authentication. Message authentication is a means of ensuring integrity of the message by providing a mechanism of verifying the source of a messageand determining if the message. 32 What is a message authentication code.
Answer 1 of 3. This module describes message authentication code MAC which is based on symmetric. 34 What properties must a hash function have to be useful for message.
Approaches to message authentication. 8 terms List three approaches to message authentication. Messa What is a message authentication code.
In all of these approaches an. 34 What properties must a hash function have to be useful for message. Approaches TO Message Authentication - supplementary reading approaches to message authentication encryption protects against passive attack eavesdroppinga Introducing Ask.
34 What properties must a hash function have to be useful for message authentication. It is a hush function that is secure to create a hash value for a message and by using a private key to. 32 What is a message authentication code.

Message Authentication Requirements Geeksforgeeks

Unit 2 Public Key Cryptography And Message Authentication Ppt Download
No comments for "Approaches to Message Authentication"
Post a Comment